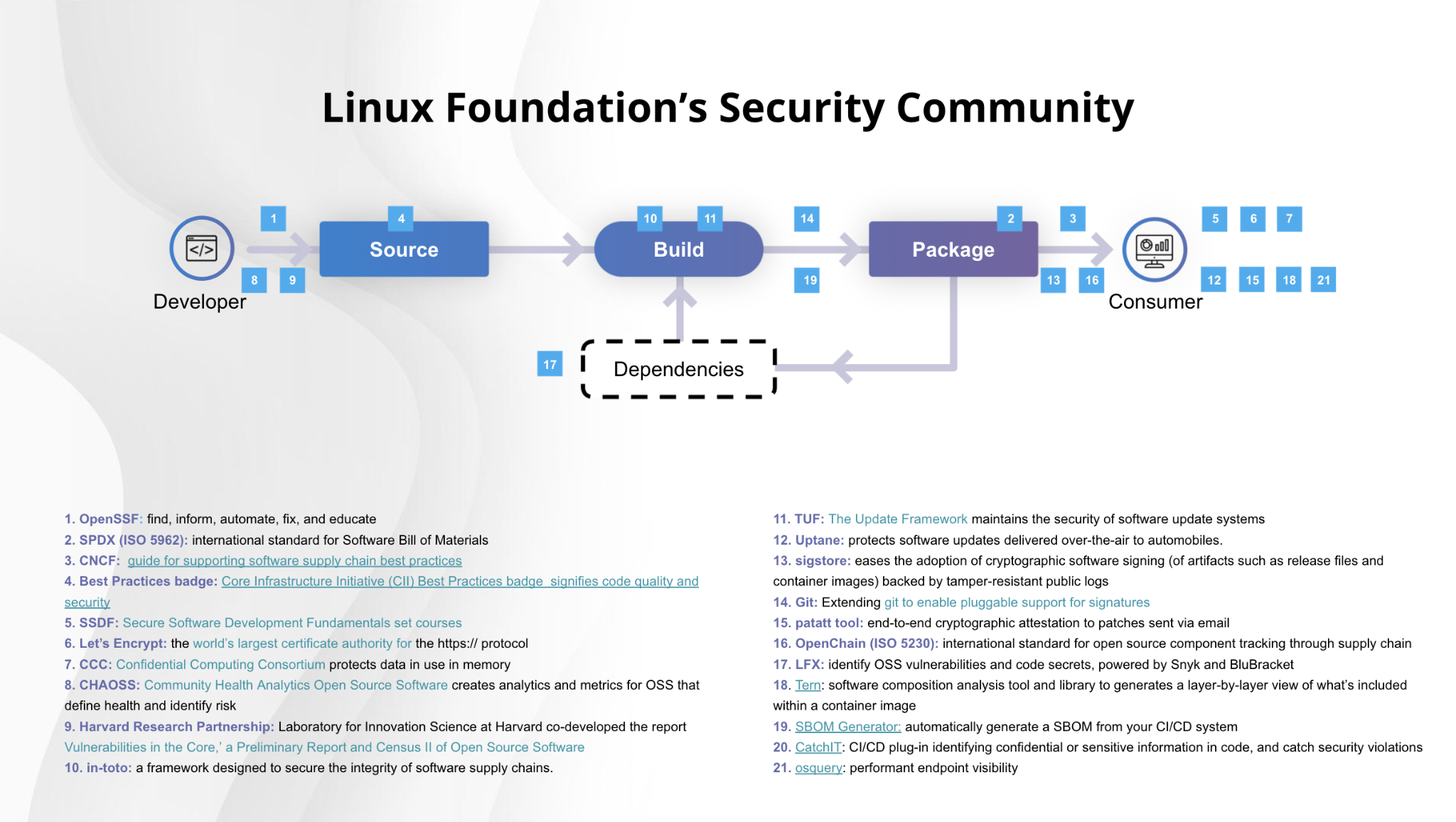
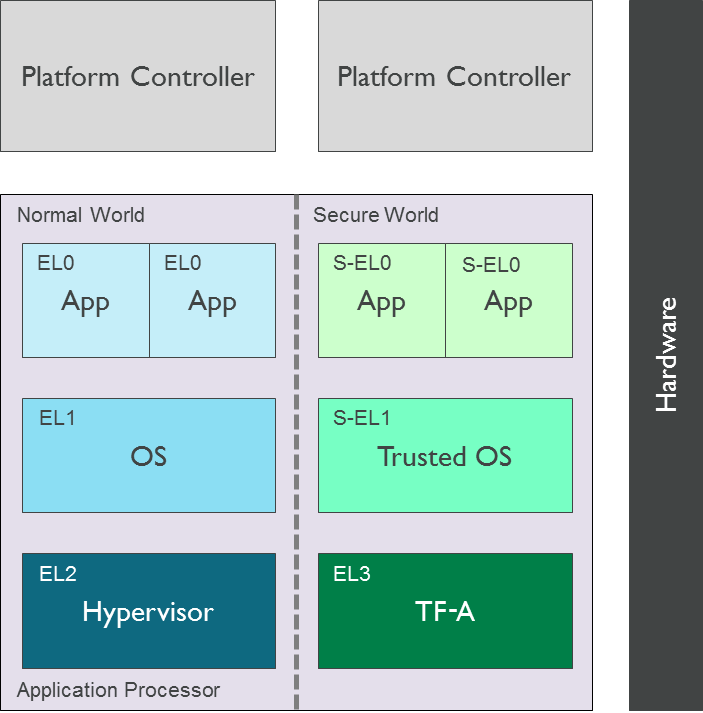
Installing and Configuring an nCipher Hardware Security Module (HSM) with FIM CM 2010 - TechNet Articles - United States (English) - TechNet Wiki

Why build a world class product security program? – Risk One – Next Generation Third Party Risk Management Platform
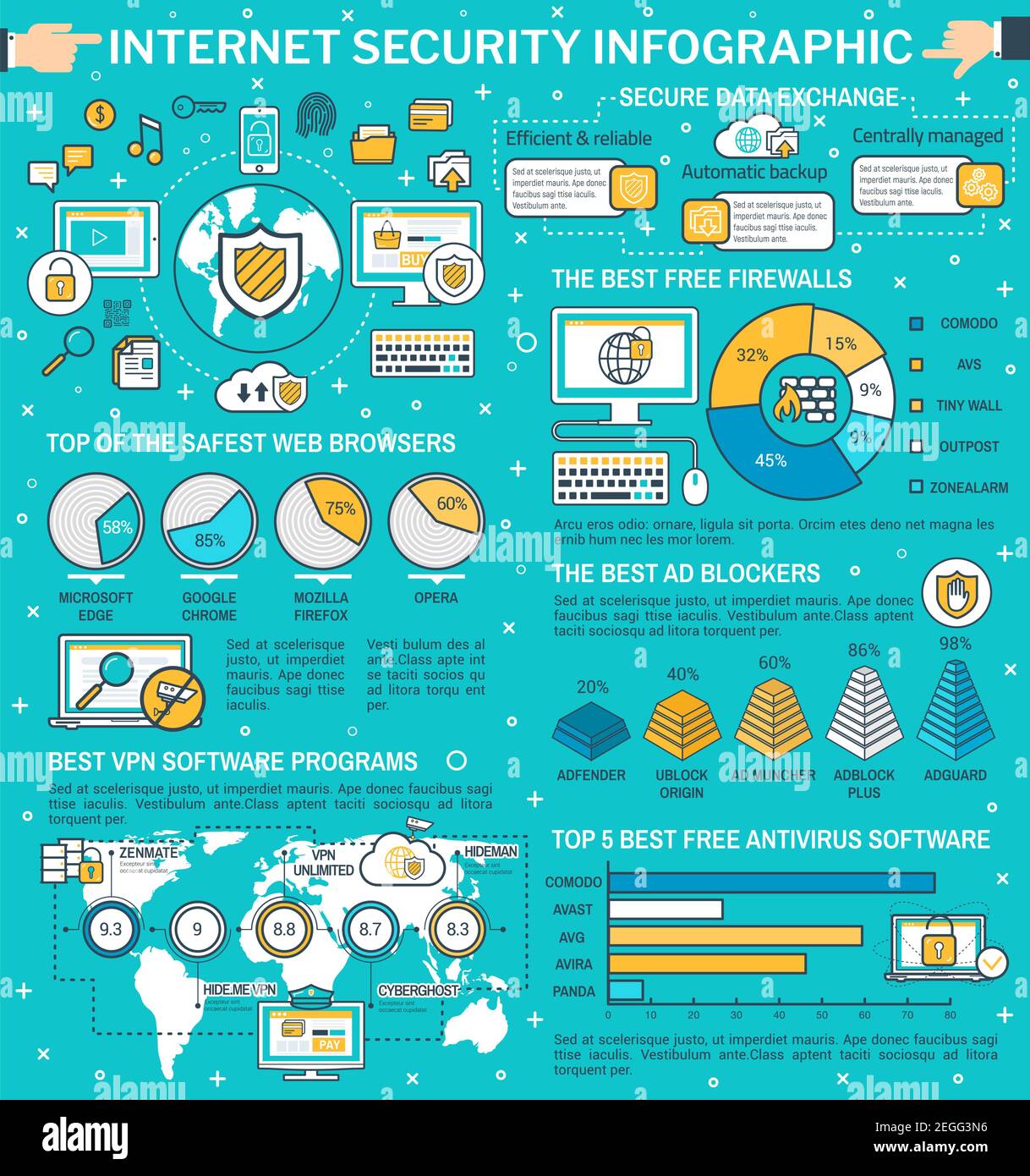
Internet security infographic design. Data protection technology graph, best antivirus software and safest browser chart and statistic world map with Stock Vector Image & Art - Alamy